A New Master’s in Business Cybersecurity
Cybersecurity Degree Principles, Packaged in a Business Degree
Introducing the online Master of Science in Business Cybersecurity degree (MSBC) from the University of Tennessee, Knoxville’s Haslam College of Business
Program Overview
Become proficient in technology and an expert in business through the online MS in business cybersecurity at Haslam. By gaining a foundational understanding of core cybersecurity tenets, you’ll be equipped to drive critical conversations around the greater implications for business strategy, operations, and resilience.
30
Total Credits
Completed 100% online
10
Courses
Flexible, part-time learning
$1,000
Per Credit Hour
Based on 2024-2025 tuition rates and subject to change each year
*Based on 2024-2025 tuition rates and subject to change each year.
Are You Ready to Lead an Emerging Field?
The term “business cybersecurity” may be unfamiliar to some. It likely won’t be for long.
Cybercrime poses one of the most pressing business threats in the digital era. It caused $3 trillion in losses in 2015—and by 2025, cybercrime will cost the global economy an expected $10.5 trillion.1 With those numbers, it’s no wonder 93% of survey respondents from the 2023 Global Cybersecurity Outlook report believe that a catastrophic cybersecurity event is bound to happen in the next two years.2
Based on current employment numbers, the world economy is unprepared to manage a crisis of such magnitude. An International Information Systems Security Certification Consortium study discovered that the international workforce needs to grow by 72% to meet the current demand for cybersecurity professionals. For a global workforce already 4.7 million strong, that translates to a gap of 3.4 million workers.3

$10.5 trillion in cybercrime-related damages expected by 2025.

93% of cyber leaders anticipate a cybercrime catastrophe in the next two years.

3.4 million professionals are needed to fill the cybersecurity workforce gap.
“Cyber resilience equals business resilience.”
Julie Sweet, Accenture Chief Executive Officer, 2023 World Economic Forum
So What Do These
Statistics Mean for You?
Accenture Chief Executive Officer Julie Sweet said it best during her presentation at the 2023 World Economic Forum meeting. She charged global leaders with understanding that “cyber resilience equals business resilience,”4 confirming the critical need for companies to develop sound business cybersecurity strategies.
That means going beyond end-to-end encryption. It means bringing cybersecurity conversations to the forefront of boardroom discussions and overall business strategy. Under Sweet’s direction, Accenture’s monthly board meetings now include a review of cyber incidents, illustrating the shift in mindset she’s urging other leaders to adopt.
That’s Where You Come In.
As more companies learn to equate cybersecurity resilience with business stability, they’ll need qualified professionals to direct those conversations and decisions.
Our innovative master’s program lays the principal groundwork of business cybersecurity concepts. Along with sound technical training, we provide graduates with the fluency to comprehend, communicate, and employ business strategies crucial to protecting data—and accordingly, the bottom line.
Together, we can give the global economy the guidance it so desperately needs. Explore our online MS in business cybersecurity curriculum below.
Curriculum
Through a combination of synchronous and asynchronous sessions, students will learn how to leverage cybersecurity foundations to better inform business strategy.
Provides students with a foundational knowledge of concepts, theories, technologies, and procedures underlying the protection of information assets. Students work with a variety of tools to enhance their knowledge and technology skills in this ever-changing area.
Designed to help students gain an understanding of the regulatory environment, governance, and ethical issues related to cybersecurity. The objective of the course is for students to understand how an organization effectively controls information technology (IT) security and manages associated ethical issues.
Provides students with an underlying knowledge of communication systems and network design. It builds on this foundation to define and identify internal and external sources of network security risk. Students will work with various tools, techniques, and methods to assess communication networks and develop and communicate mitigation strategies to reduce network and overall cybersecurity risk.
Introduces the components, processes, and techniques associated with protecting organizational information assets. Students will work with a variety of modern database management and monitoring tools to develop business and technical skills related to management and protection of a broad range of information assets.
Introduces the process and techniques of corporate risk management and business continuity, including its major activities such as risk assessment, risk mitigation, and risk control. Students will learn how to assess, develop, and implement effective risk management practices to meet business continuity objectives.
Provides students with an understanding of the human and organizational aspects of security and methods to mitigate risks associated with these areas. Students will work with various tools, techniques, and methods to assess organizational security practices and develop and communicate strategies to reduce overall cybersecurity risk.
Covers the fundamentals of designing and implementing a multi-tier security architecture, focusing on the processes and tools used to protect assets and resources housed on organization servers. Students will work with a variety of tools and techniques to develop knowledge and technical skills related to the assessment, design, and management of an organization’s security architecture.
Designed to help students gain a fundamental knowledge of secure software development practices. The objective of the course is for students to understand how an organization formulates and manages software development processes where security is built in and ensures confidentiality, integrity, and availability in software applications. Students will work with various tools, techniques, and methods associated with the development, implementation, and management of organizational software applications.
A seminar designed to spotlight and examine technology innovations that are impacting (disrupting and transforming) the dynamic field of business cybersecurity. The course will focus on the potential opportunities and risks associated with trending and emerging technologies.
Enables students to integrate their learning from all prior coursework. Students will work on a broad array of contemporary cybersecurity problems and issues experienced by organizations. Students will have the opportunity to assess, analyze, and solve cybersecurity problems and present their results and solutions as aspiring cybersecurity managers.
The Online Learning Experience at UT
At UT Knoxville, we understand the importance of real-world practice for your future success. That’s why our online MSBC program offers both live and asynchronous learning opportunities tailored to your needs.
Live and Interactive
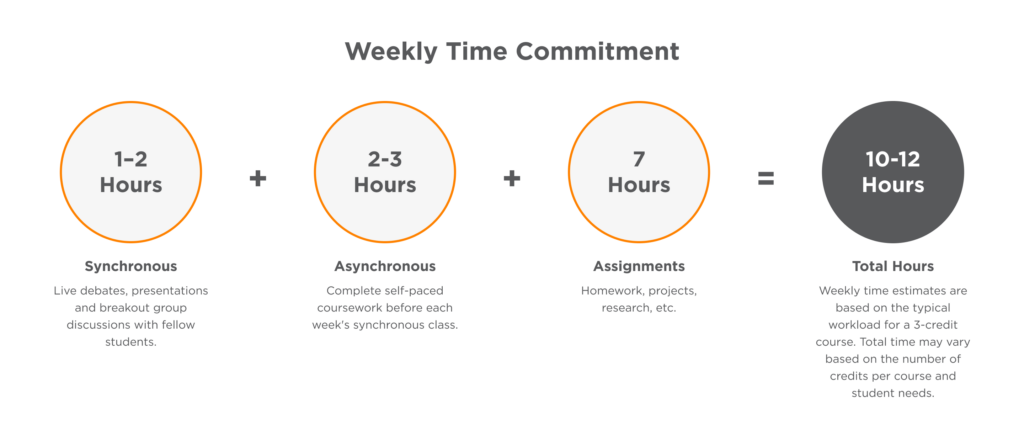
Engage in real-time debates, presentations and group discussions with fellow students. Our program blends technology, curriculum and partnerships for career-ready skills.
Take Less and Achieve More
Each semester, students typically take two courses, with either weekly 60-minute or biweekly 120-minute synchronous sessions usually held on weekday evenings EST. This amounts to six to 12 sessions per class per semester.
Efficient Learning
Our learning management system (LMS), Canvas, serves as the one-stop shop for all course content and activities. Manage projects, assignments and communication with instructors and classmates seamlessly. Typically, you can expect about 6–10 hours of work outside classes each week.
Admissions Overview
Ready to join the Volunteer community? Our streamlined application aims to recruit impassioned master’s candidates by focusing on a few key components: a personal statement, a resume or CV, and undergraduate transcripts. That’s right—we don’t require any standardized tests or letters of recommendation. Review our complete admissions process and begin your application today.
Apply Now Watch an Application OverviewKey Dates
Upcoming Events
Check back soon for more upcoming events.
On-Demand Content
Cybersecurity Degree FAQs
Looking for an answer not listed on our site? Connect with our team today to get answers to your top questions.
Email the enrollment teamBusiness cybersecurity is the intersection of business principles and cybersecurity strategies aimed at protecting organizational assets, data and systems from cyber threats and attacks.
Our online Master of Science in Business Cybersecurity program equips students with the knowledge and skills to navigate this dynamic field, combining technical expertise with business acumen to address the evolving challenges of cybersecurity within organizational contexts.
We do not require a technical background to apply to the online MSBC.
Students from all academic and professional backgrounds will be considered for admission to the online MSBC program. Applicants should have a basic interest and understanding of cybersecurity foundations and their business applications.
No, we do not require GMAT or GRE scores for admission to the online MSBC program.
To apply to the online MSBC program, applicants must submit:
- A personal statement
- A resume or CV
- Undergraduate transcripts
Our streamlined application process aims to simplify the path to joining our vibrant community of learners, empowering students to focus on their academic and professional goals. Schedule a one-on-one walkthrough with your enrollment advisor to learn more about the program and application process.
Yes, international students are eligible to apply; they must submit a Test of English as a Foreign Language (TOEFL) score with their application materials. Please note that international students enrolling in fully online master’s programs like the MSBC are not eligible to receive sponsorship for an F-1 visa.
As a part-time student, you can complete the degree in as few as two years. However, the program is designed to be flexible, allowing you to take courses at your own pace and earn the degree over a span of up to six years.
Yes, students can pursue the program on a part-time basis. With the flexibility of part-time learning options, students can balance their academic pursuits with other commitments, allowing for a personalized approach to earning their degree.
Online MSBC graduates will be prepared to plan and communicate a synthesized business and cybersecurity strategy. The 3.4 million job gap underscores the industry’s demand for skilled individuals. In fact, professionals can expect an average salary of $120,000 in this field. The following list of potential career paths offers a glimpse into the diverse opportunities available to MSBC graduates.
- Business cybersecurity analysis
- Cybersecurity consulting
- Business cybersecurity risk mitigation
- Cybersecurity auditing
In addition to providing guidance on the application process, enrollment advisors can answer questions about scheduling, curriculum, student experience and more. Schedule a one-on-one walkthrough with your enrollment advisor to learn more.
We understand that financing your education is a crucial aspect of your academic journey. Our online business cybersecurity students have access to a range of financial aid options, including federal financial aid, military aid and employer sponsorship. Our dedicated financial aid team is here to guide you through the process and help you explore all available opportunities.
Are You Ready To Drive the Future of Business Cybersecurity? Start With UT Knoxville.
Apply Now- 1 Cybersecurity Ventures, 2020
- 2 Forbes, 2023
- 3 International Information Systems Security Certification Consortium, 2022
- 4 Forbes, 2023